So let's start with the basics. You are on call, you receive this alert, the first question you might ask yourself.
What is a Playbook?
A playbook is a predetermined set of instructions and rules known as an incident response playbook describes how to identify, address, and recover from particular kinds of cybersecurity issues.
It offers detailed guidance on how to respond to threats like as malware infections, data breaches, and system outages. By doing so, you can minimize damage and downtime and ensure that responses are prompt, well-coordinated, and effective.
- Head over to the Investigation Channel tab.
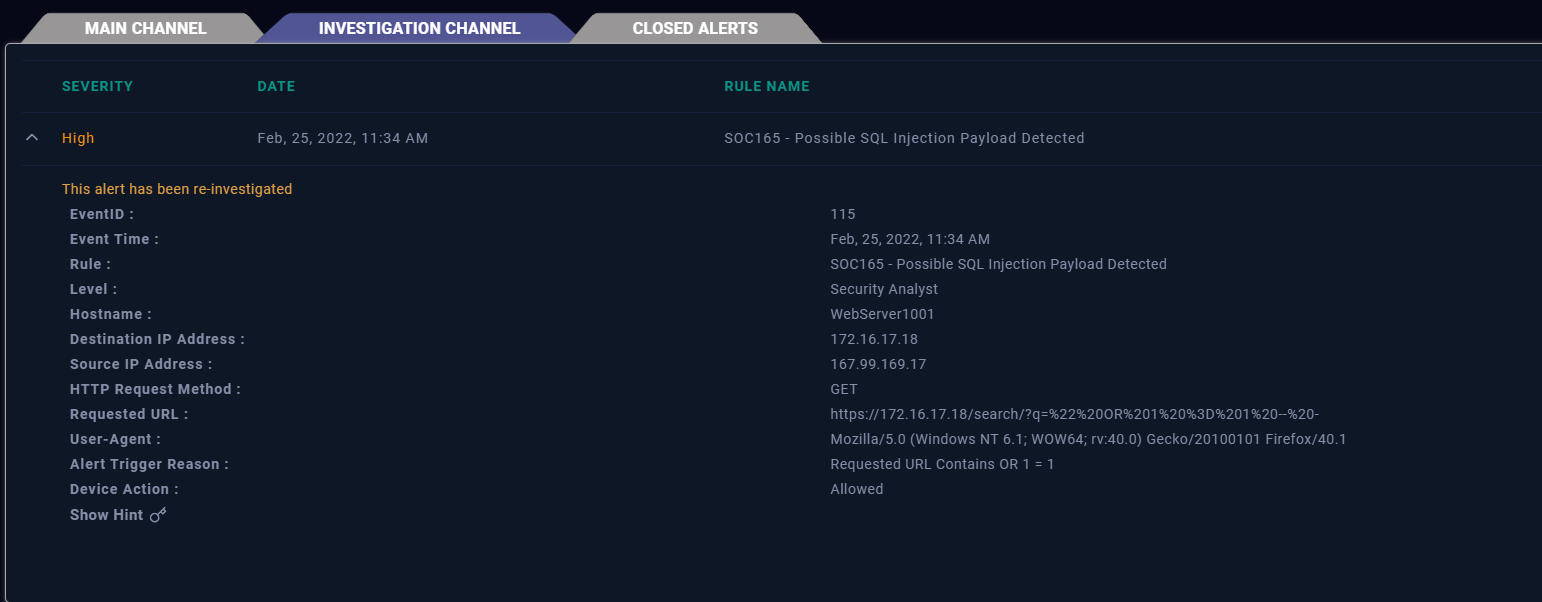
We will get a detailed output of the event, let's filter out the noise and jot down the important details:
Hostname :WebServer1001
Destination IP Address :172.16.17.18
Source IP Address :167.99.169.17
Method: GET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.1
Trigger Reason: OR 1 = 1 - payload
So with this information we can start our investigation.
2. Navigate to Log Management, on your sidebar.
- Click over below the New Search bar, and it will automatically let you populate a filter. Apply the following two filters:
Column: Source address
Operator: Contains
Value: 167.99.169.17
Column: Destination address
Operator: Contains
Value: 172.16.17.18
- Once the two filters have applied, you should get 6 SIEM events.
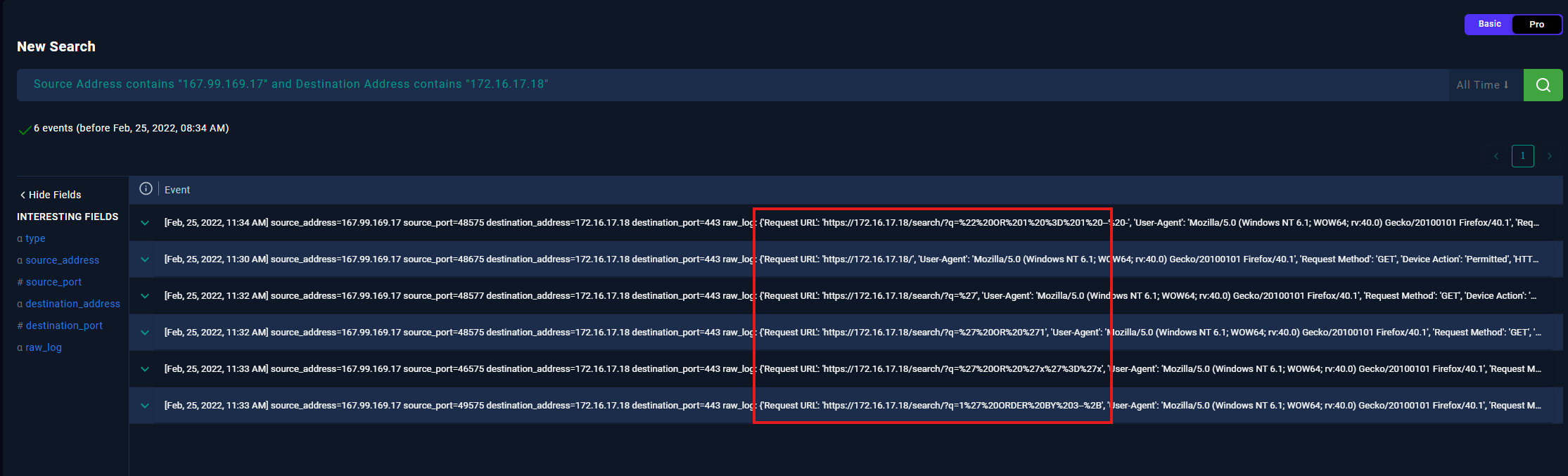
- At first sight, you may be able to see that the request URL contains SQL injection payloads. If you expand on one of these events, you will be able to see the full log, in detail.
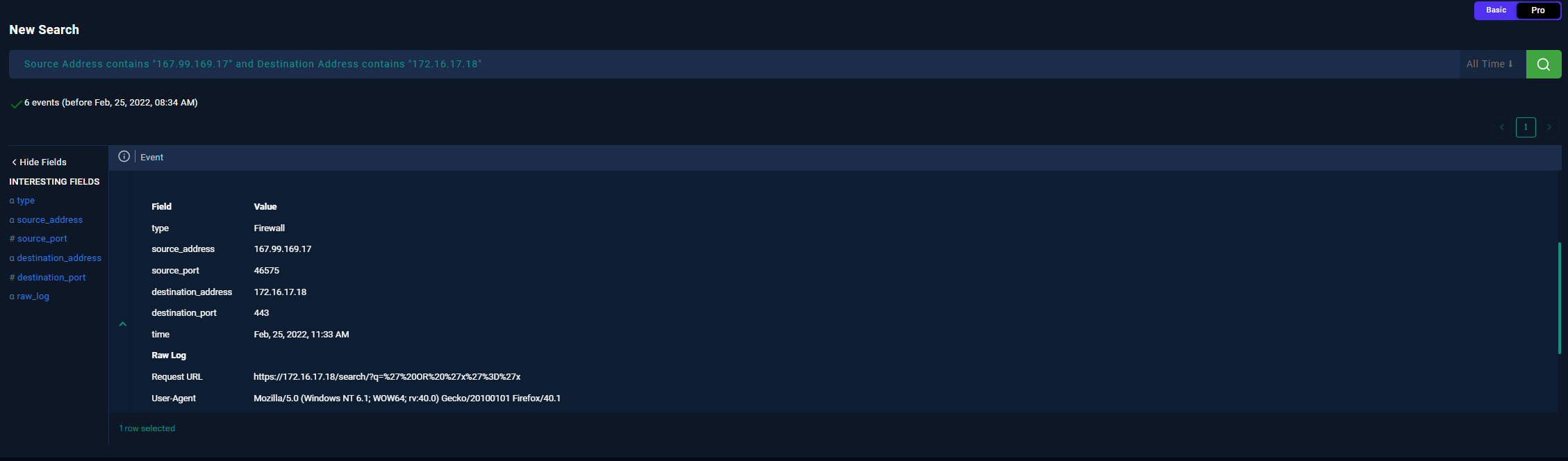
- Up until here, we can return to our playbook and confirm this is malicious traffic.
If we remember, the payloads seen in the SIEM were:
Payload: ' OR 'x'='x
URL: https://172[.]16[.]17[.]18/search/?q=%27%20OR%20%27x%27%3D%27x
Payload: " OR 1 = 1 -- -
URL: https://172[.]16[.]17[.]18/search/?q=%22%20OR%201%20%3D%201%20--%20-
Payload: '
URL: https://172[.]16[.]17[.]18/search/?q=%27
Payload: ' OR '1
URL: https://172[.]16[.]17[.]18/search/?q=%27%20OR%20%271
Payload: ' OR 'x'='x
URL: https://172[.]16[.]17[.]18/search/?q=%27%20OR%20%27x%27%3D%27x
Payload: 1' ORDER BY 3--+
URL: https://172[.]16[.]17[.]18/search/?q=1%27%20ORDER%20BY%203--%2B
The enumerated payloads demonstrate various SQL injection (SQLi) techniques aimed at manipulating SQL queries in a web application's database. For example, the payloads like ' OR 'x'='x and " OR 1 = 1 – - introduce logical conditions that always evaluate to true, enabling attackers to bypass authentication or access unauthorized data.
Other simple inputs, such as a single quotation mark ('), attempt to break the original query structure, allowing attackers to execute arbitrary SQL commands. These payloads highlight the vulnerabilities of poorly secured input fields, which can lead to unauthorized access and data exposure.
- Let us head over to the Email Security Tab and double check in case this is a pentest or a drill from the SIRT that we might have overlooked. When it comes to cybersecurity, it is better to be too cautious than too cautious.
Perform a detailed search using the IP address of the destination, and origin source, use the hostname of the machine: Webserver1001.
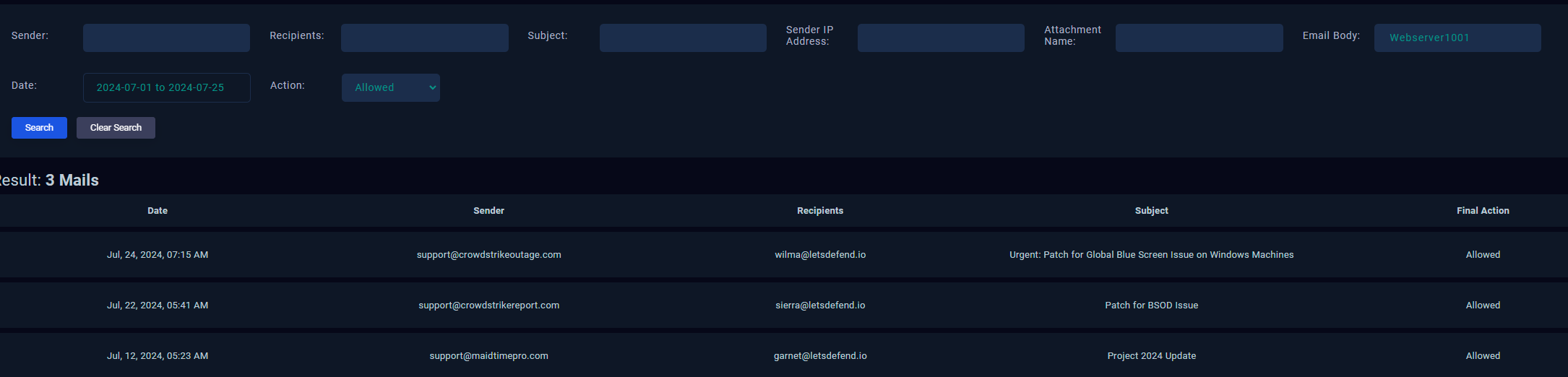
- Generally, we want to select a date before the incident timeline, which was anywhere before the 25th. I have also searched the hostname within the email body; however, even with these 3 results, it seems there is no planned test.
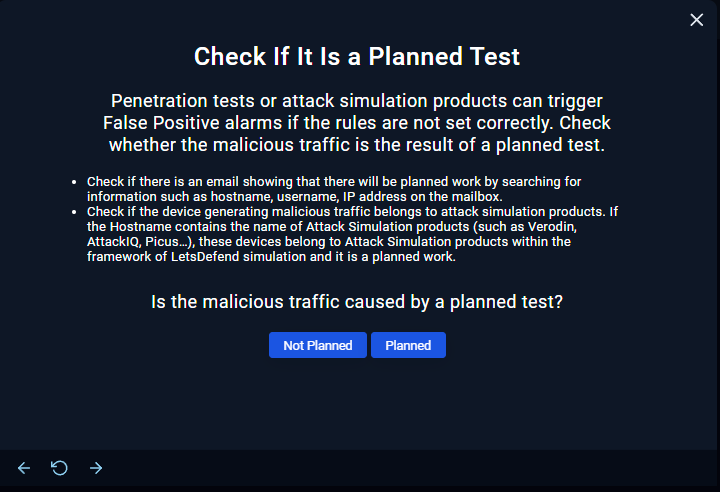
So now, following the playbook, we will get the following question:
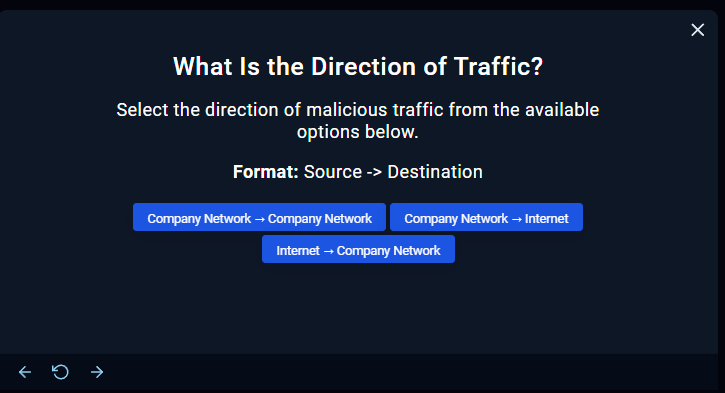
- Let's recall earlier:
Column: Source address
Operator: Contains
Value: 167.99.169.17
Column: Destination address
Operator: Contains
Value: 172.16.17.18
The destination address (specifically, the 172.16.0.0 to 172.31.255.255 range) belongs to a private IP network, so this must be a company site. While, the source address is a public IP address, this is the internet.
Thus, if the destination is the company's internal network and the source is the internet, it indicates that we were infiltrated from an external source.
Let's review whether the attack was successful or not.
- Navigate to Endpoint Security
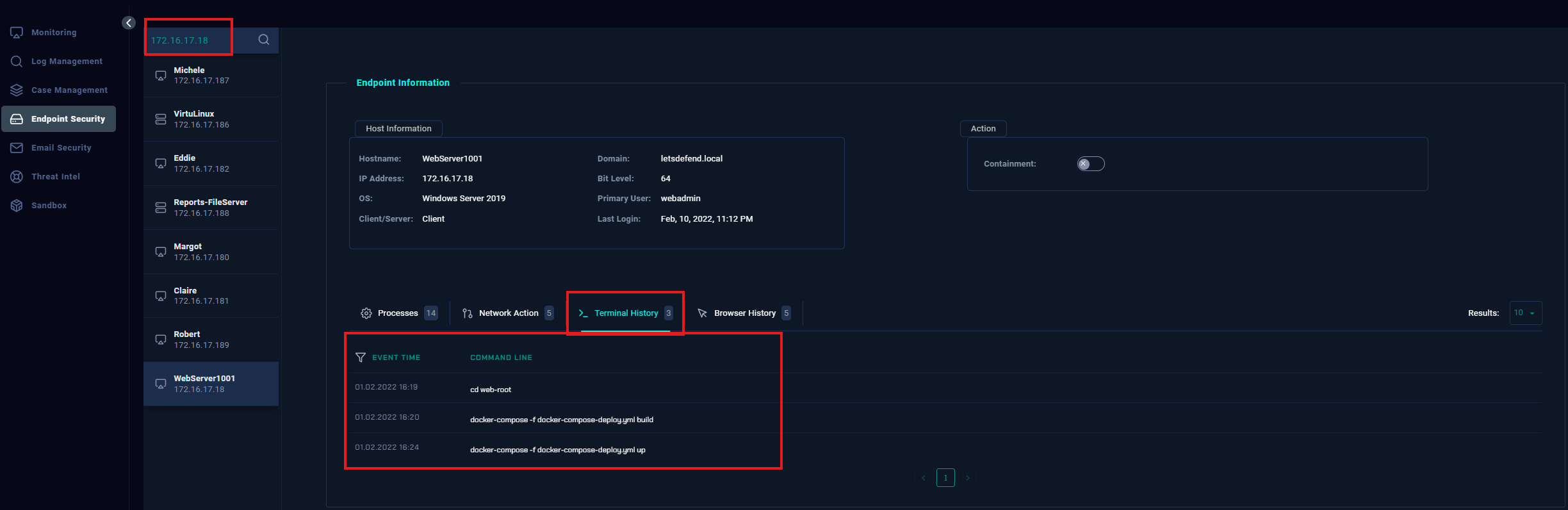
- In this case, we will filter by the endpoint address, specifically the destination address (172.16.17.18) and then review the terminal history to check for any abnormal activity.
Note: They look like Docker commands to me, if this were a real scenario, you would inspect the .yml build just to make sure they are not launching a malicious app and contact the dev team to make sure those are expected pods to be running.
- We have now determined that the attacker's SQL attack was unsuccessful, but the SIEM recorded the attempt. Next in our list is to add the Artifacts.
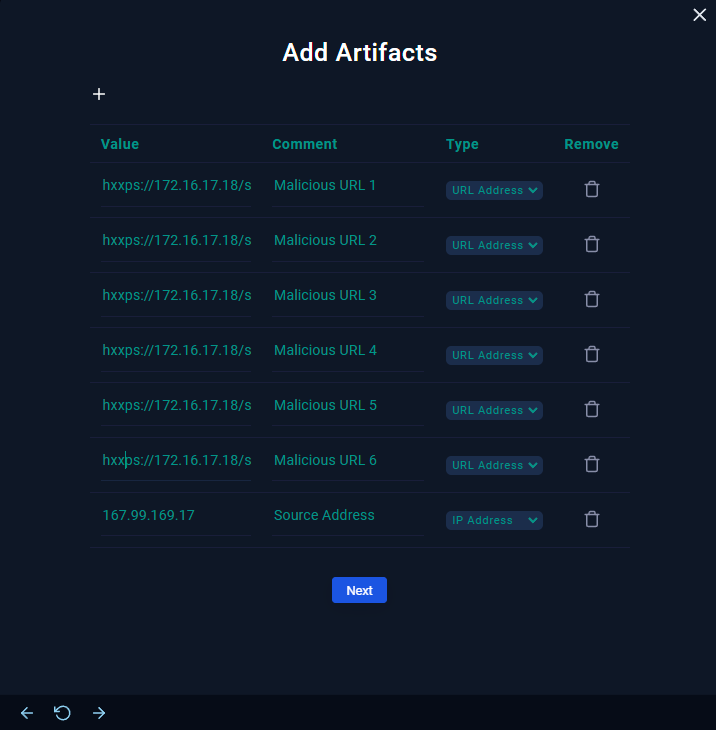
Any information or proof gathered while looking into a security incident or breach is referred to as an artifact in the field of cybersecurity.
These artifacts may consist of a variety of objects, including:
- Log files
- Data packets
- Code or executable files
- File System Data
- Memory dumps
- Configuration files
- User Activity Data
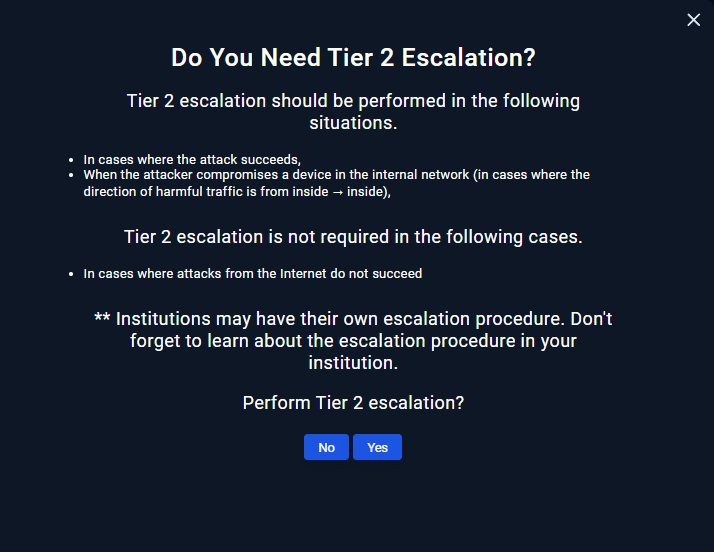
- A Tier 2 analyst, typically found in cybersecurity operations centers (CSOCs) or IT support teams, is a mid-level professional who handles more complex issues that surpass the capabilities of Tier 1 analysts. In this case It's important to identify if there was a breach or not, if there was not do not escalate it, if you are unsure it's best to escalate to discard.
Answer: No
- You will then be presented with a comment section. We will enter all the information pertinent to the case that the playbook did not address in this section.