Overall Get Ready
The goal of such a method is to provide guidelines for handling events or threats to the current company or its partners in the event that they escalate into a crisis. It's critical to realize that a cyber crisis has no set definition. Depending on the effect on output and the organization's degree of functioning, each organization will define a crisis differently. The management of security incidents and crises is governed by various standards, including:
- NIST SP 800-34: the beginning of the crisis
- ISO 27035: ensuring the security
- ISO 22301: continuity management system
A cyber crisis isn't only a technical problem; it affects more than just IT personnel. In such cases, you should be aware of the following: Your team won't be able to get over its ransomware problem in a few hours. It will take a while to gather the information you'll need to review.
Deadlines are in-compressible in certain situations. It takes an in-compressible amount of time to travel to a distant data center to manually intervene on a server. Making adequate preparations in advance for a cyber disaster is among the first things to undertake. As a result, we will walk you through a flow of several phases.
A list of all the resources you have
It's critical to keep a list of all the technological and human resources you have on hand in case of emergency. You must ensure that this list contains the responses to the following inquiries when you are compiling it:
- Do you have technical staff members specifically assigned to incident response?
- Are your employees trained?
- Are there any requirements for the personnel who will be called upon?
Routes of communication
It's imperative to have a secure communication channel apart from your infrastructure in case your organization gets compromised.
Protection
Insurance is one of the important topics that is frequently brought up at the conclusion of remediation. Please take note of the following headings when making the insurance.
Do You Feel Safe?
Finding out if you are protected from cyber-related problems should be your first priority. We must confirm the scope of our coverage.
Maximum Assist?
As previously stated, defining what is covered by your insurance is the most crucial thing to confirm. Will your insurance, for instance, cover a ransom for systems that have been infected with ransomware? Typically, insurance companies only pay for the costs associated with things returning to normal; they do not cover renovations or other costs such as overtime paid to employees or equipment purchases, among other things.
Partners
Lastly, it's critical to understand if the insurance provider will designate a specific representative for handling cyber emergencies. This is an important aspect because you will require extra care in these situations, therefore we should confirm whether our insurance provider is giving you that kind of care.
In cybersecurity incident response, having the right tools is essential for effective investigation and analysis. Here’s a concise list of free and open-source tools that can enhance your capabilities during a crisis. These resources, ranging from specialized Linux distributions to automated analysis scripts, are invaluable for gathering evidence and assessing incidents efficiently.
Linux Caine
Giovanni "Nanni" Bassetti is the manager of an Italian live Linux distribution. The project began in 2008 as an environment that included many pre-installed tools for incident response and digital forensics.
TSURUGI Linux
A DFIR open source project, Tsurugi Linux is and will always be completely free and autonomous, excluding all commercial brands. They claim that imparting information and "giving back to the community" are their primary objectives.
Investigator forensic
This script uses programs like "winpmem" and others to automate the gathering of data.
Visit the tool's webpage.
Time-stamped Netstat
You can observe the connections with the timestamp indicator thanks to this script. An essential item!
Visit the tool's webpage.
Mandiant RedLine
Through the integration of indicators of compromise (IOC) generated by Mandiant's free IOC Editor tool, Mandiant's free Redline tool facilitates quick memory analysis.
Visit the tool's webpage.
Velociraptor
The velociraptor is a much too useful weapon. It makes it possible to retrieve workstation data, including RAM and CPU usage, among many other things. Investigating using its interface to examine the contents of prefetches, event logs, extract RAM, and other things is also beneficial.
Visit the tool's webpage.
APT Scanner THOR
A feature-rich YARA and IOC scanner to automate assessments of compromise
Visit the tool's webpage.
In responding to a cyber crisis, it's essential to mobilize both a Management Unit and an Operational Unit. The Management Unit sets strategic priorities for the response, directing the Operational Unit on what to remediate and restore first. This unit also handles internal and external communications, addresses concerns from various departments, and manages the overall impact of the crisis. Their decisions encompass critical aspects, such as employee compensation during downtime and communication strategies with customers and the press.
The Operational Unit focuses on two key tasks: reconstructing the internal infrastructure for incident response and restarting business operations as directed by the Management Unit. Comprising technical experts, this unit is responsible for identifying the source of the compromise, determining the date of initial intrusion, and generating Indicators of Compromise (IOCs). These efforts are vital for understanding the attack and ensuring that newly restored systems are free from vulnerabilities that previously led to the incident.
As the investigation progresses, the Operational Unit will also work on rebuilding the infrastructure in isolation and implementing stronger security measures. While achieving 100% security is nearly impossible, the lessons learned from the crisis highlight the need for more stringent hardening processes to prevent future compromises. Ultimately, the Management Unit will decide when the organization can transition back to normal operations, marking the end of the crisis response phase.
The Importance of Backups in Cyber Resilience
Effective backup management is crucial for ensuring a quick return to normalcy after a cyber incident. However, it's important to note that backups are not a protective measure on their own; a poor backup policy can jeopardize an entire business. Regardless of whether backups are stored internally, on external drives, or in the cloud, they must always be encrypted, with decryption keys stored securely outside of your organization's IT systems.
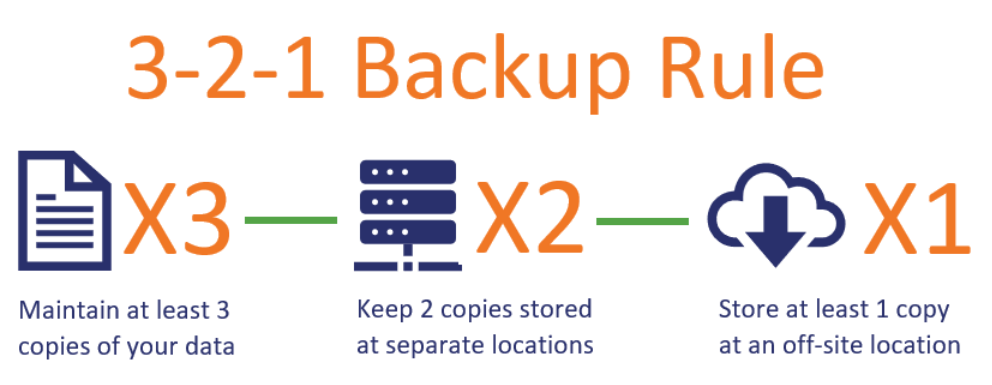
A foundational principle for backup strategies is the 3-2-1 rule: maintain at least three copies of your data, store them on two different media, and ensure one copy is kept off-site. This approach safeguards against data loss due to hardware failure, data corruption, or local disasters, such as fires. For critical resources, consider the 3-2-1-1-0 rule, which adds two additional requirements: one offline backup that is disconnected from your network and regular testing to ensure error-free restoration.
By adhering to these guidelines, businesses can significantly enhance their resilience against cyber threats and ensure that they can recover swiftly and effectively when incidents occur. Regularly reviewing and updating your backup strategy is vital to maintaining this preparedness.
Alert Your Partners
Keep in mind that you are not alone. If your information system is compromised, you can become a threat to your partners interconnected with your network. Similarly, perhaps the attacker has come from one of your partner’s networks and you, being more prepared, has detected it while your partner failed.
In any case, communicating with your partners is a good practice.
Alerts and Managing the End of a Crisis
In the aftermath of a cyber incident, it’s crucial to know who needs to be alerted, the time-frame for those alerts, and who is responsible for notifying them. This varies by organization, regulatory standards, and location. Additionally, inform your partners about the breach, as their networks may also be at risk, and they could have insights into the origin of the attack.
When the crisis is resolved, follow a clean desk policy by securely destroying all notes and documentation related to the incident. However, consider preserving encrypted files from ransomware attacks in offline storage in case encryption keys become accessible later.
Finally, as pressure subsides, maintain vigilance by overseeing your new infrastructure and staff. Be cautious of service providers eager to offer continued support or solutions; take time to evaluate your options before committing.
