Your team is working on setting up a Kubernetes cluster with two controllers and two worker nodes. In order to ensure that the cluster is configured securely, the team wants to enable the feature that allows Kubernetes to encrypt sensitive data at rest. In order to accomplish this, the team needs a Kubernetes data encryption config file containing an encryption key. Your task is to generate an encryption key and create this file, then copy the file to the two Kubernetes master servers.
- We will generate a system variable:
ENCRYPTION_KEY=$(head -c 32 /dev/urandom | base64
This command generates 32 random bytes from /dev/urandom (a source of cryptographic-quality random data) and encodes them into a Base64 string.
The result is stored in the ENCRYPTION_KEY variable for use in encryption or cryptographic processes.
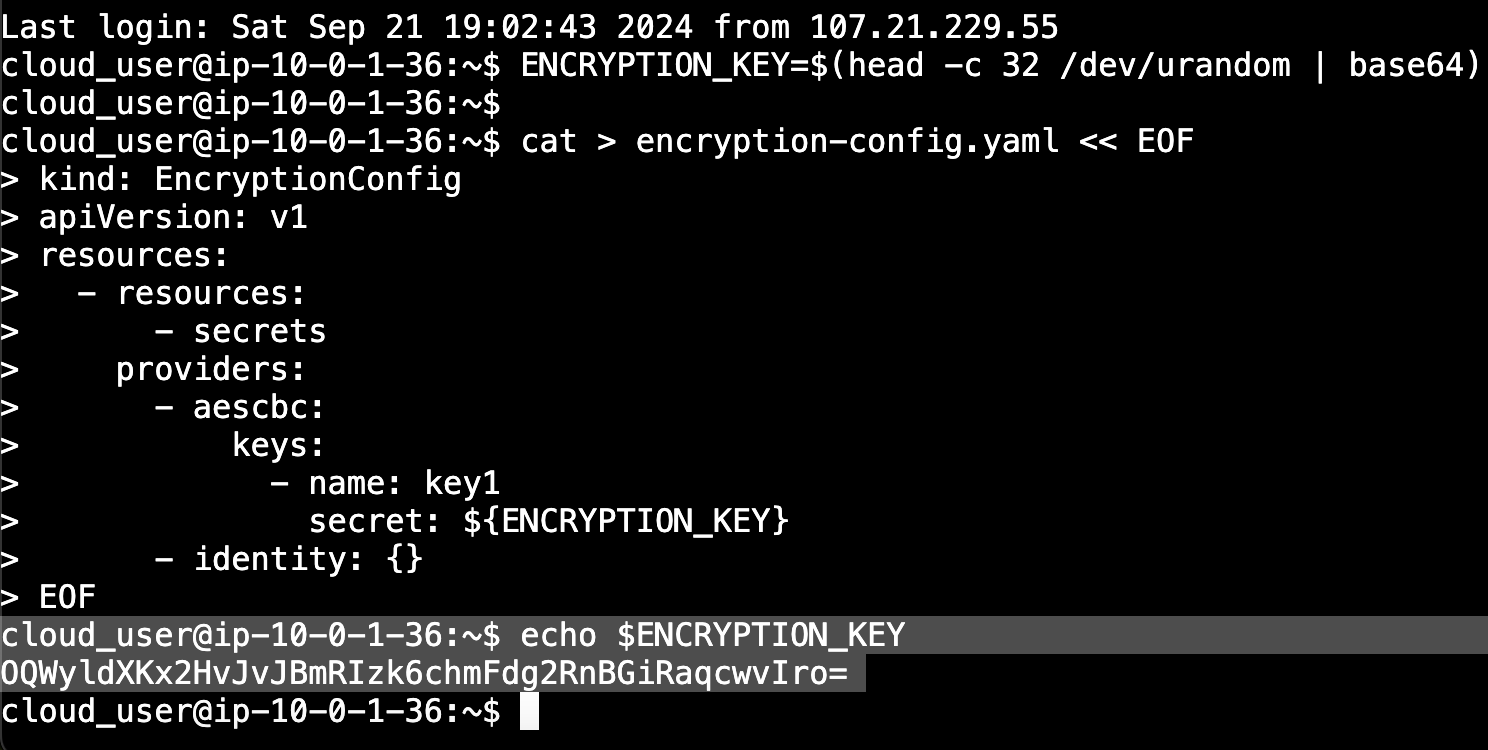
The environment encryption key can be called by performing an echo command, and it will notify us what encryption key will be used in the encryption-config.yaml we will create next.
cat > encryption-config.yaml << EOF
kind: EncryptionConfig
apiVersion: v1
resources:
- resources:
- secrets
providers:
- aescbc:
keys:
- name: key1
secret: ${ENCRYPTION_KEY}
- identity: {}
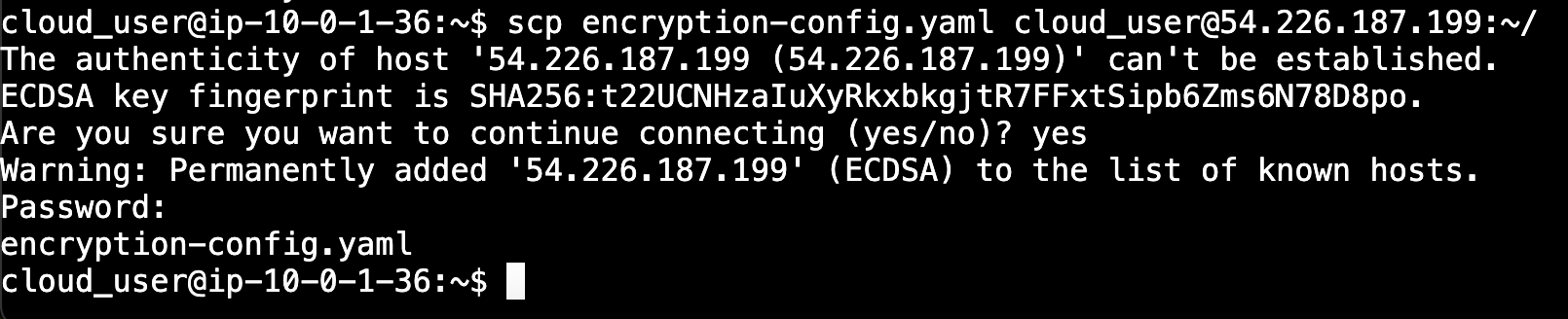
EOFSo once we have executed our configuration file, and it is saved, we will copy this file over to server controller 0 and server controller 1
First, we will copy it over to server controller 0
scp encryption-config.yaml [email protected]:~/
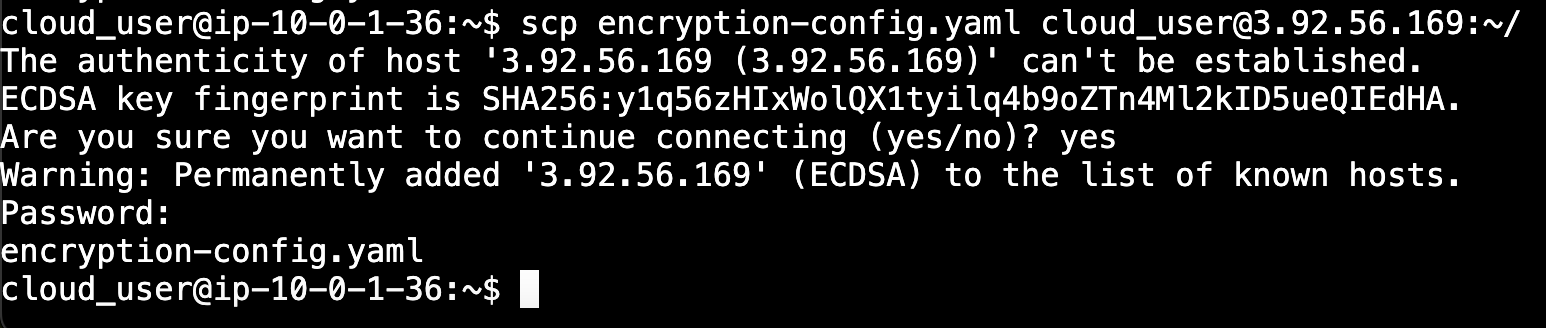
Now we will copy it over to 3.92.56.169, which is server controller 1
Enabling data encryption at rest is a crucial security measure when configuring a Kubernetes cluster, especially in production environments. By using an encryption key stored in the encryption-config.yaml file, sensitive data such as Kubernetes secrets are protected from unauthorized access, even if attackers manage to compromise the underlying storage systems.
The provided process generates a strong encryption key using a cryptographically secure random number generator and encodes it in Base64, ensuring robust encryption. The configuration file then specifies AES-CBC encryption for Kubernetes secrets, along with a fallback identity provider for unencrypted data. Securely copying this file to both Kubernetes controllers ensures consistent encryption across the cluster, safeguarding the integrity and confidentiality of sensitive data stored at rest. This approach not only helps meet compliance requirements but also fortifies the cluster against potential data breaches.