These are personal notes from my ongoing pursuit to obtain the CISSP certification sometime in 2025.
Risk management is the identification, assessment, and prioritization of risks and the economical application of resources to minimize, monitor, and control the proability and/or impact of these risks.
Risk management steps: value, risk, and treatment.
Types of analysis that can be performed:
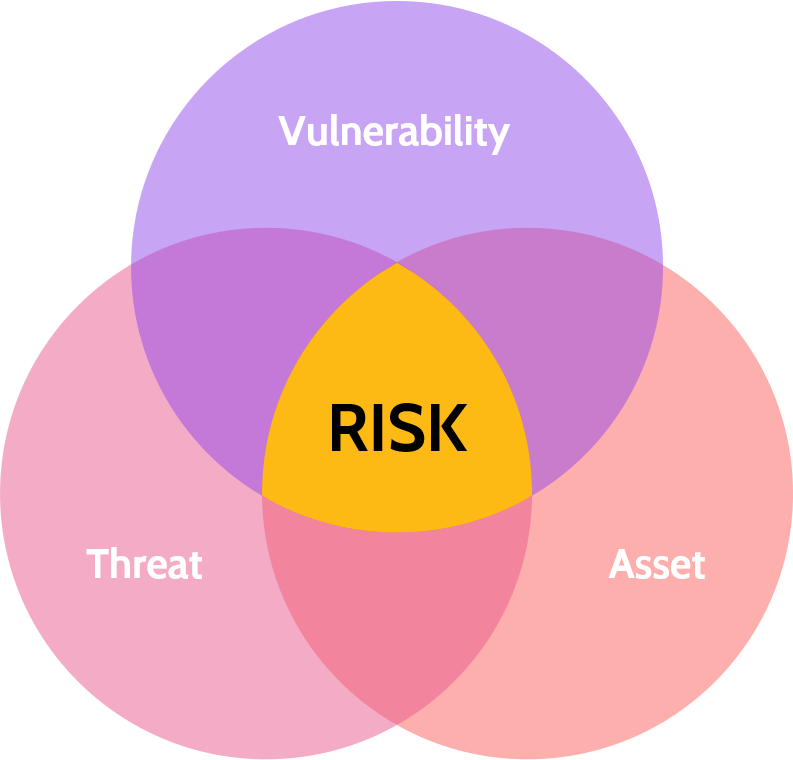
There are three main components to a risk being present:
- Asset: anything of value to the organization
- Threat: any potential danger; anything that causes damage to an asset, like hackers, earthquakes, ransomware, social engineering, denial-of-service attacks, disgruntled employees, and many others.
- Vulnerability: a weakness that exists; anything that allows a threat to take advantage of it to inflict damage to the organization. Examples include open ports with vulnerable services, lack of network segregation, lack of patching, and OS updating
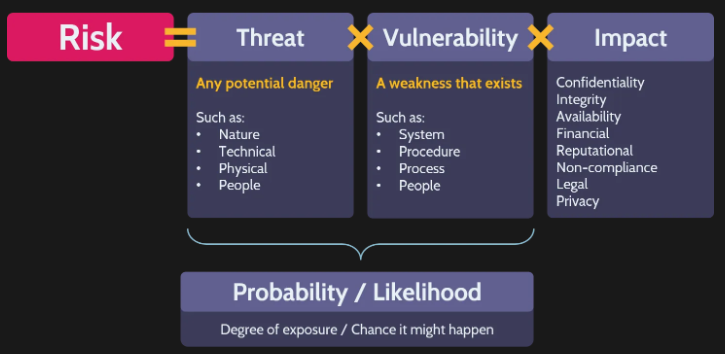
So what is a risk analysis?
- Process of identifying threats and vulnerabilities related to an asset.
Identify risks and understand the probability/impact of risk occurring.
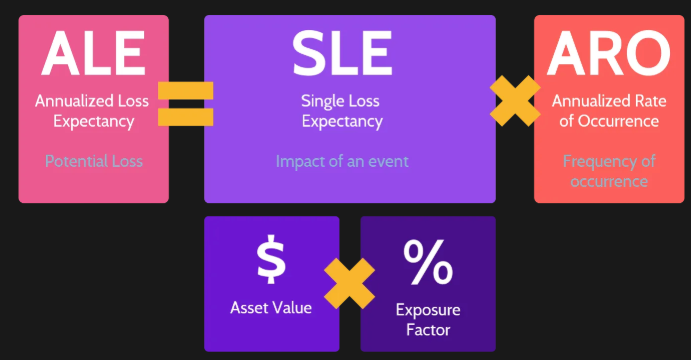
What is Single Loss Expectancy? Formula for calculating the estimated financial loss for a specific risk occurring once:
SLE = Asset Value * Exposure Factor
Calculated by Multiplying Asset Value by Exposure Factor
Annualized Rate of Occurence Formula for calculating the estimated annual financial loss for a specific risk: ALE = SLE * ARO
(Frequency of occurrence) x Asset Value x Exposure factor
ARO, how many times would you expect it to occur?
If you multiply the SLE (Single loss expectancy x ARO) = ALE (Annualized loss expectancy),
ALE = SLE(AV x EF) x ARO
Definitions of the five components of this formula are as follows, using a CCTV system as an example throughout:
- Asset Value (AV): The cost of the asset in a monetary value, e.g., a CCTV system that costs $2,000.
- Exposure Factor (EF): Measured as a percentage and expresses how much of the asset’s value stands to be lost in case of a risk materializing, e.g., if the voltage spikes excessively during certain periods of the year, a CCTV might lose three cameras to damage, thus costing $200. This represents 10 percent of the total cost (which is $2,000) and thus makes the EF be 10 percent. The EF will always be a percentage between 0 to 100 percent.
- Single Loss Expectancy (SLE): Denotes how much it will cost if the risk occurs once. To calculate the SLE, simply multiply the AV by the EF: SLE = AV * EF, which in this example becomes $2,000 * 10 percent = $200.
- Annualized Rate of Occurrence (ARO): Denotes how many times each year the risk is expected to occur. For example, if the voltage spikes excessively three times a year, the ARO is 3.
- Annualized Loss Expectancy (ALE): Expresses the annual cost of the risk materializing. To calculate it, use the following formula: ALE = SLE * ARO, which in this example becomes $200 * 3 = $600.
Risk Treatment
- Avoid: Avoid the risk; risk avoidance.
Downside: Opportunity Cost
- Transfer: Purchase an Insurance
- Mitigate: Put in place controls to reduce the risk
- Accept: The owner of the asset accepts the risk.
We would accept the risk if the controls are not cost-justified.
Who is accepting the risk? The data owner.
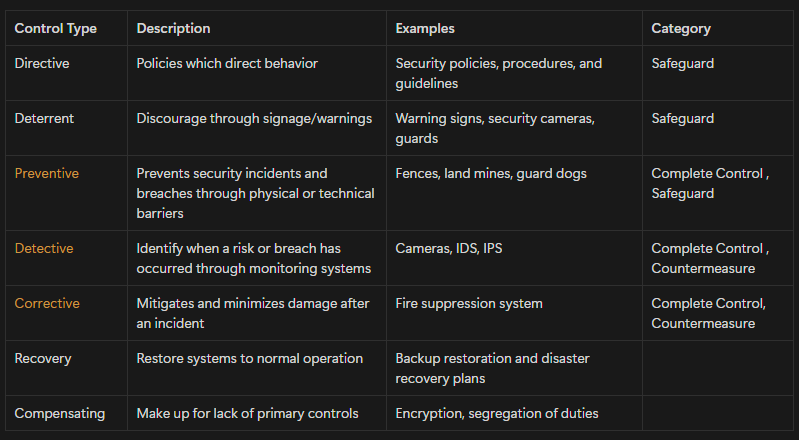
Controls:
| Control Category | Description | Examples |
|---|---|---|
| Safeguards | Controls used to prevent risk | Preventive measures, security policies |
| Countermeasures | Controls to detect & respond to risks | IDS, IPS, incident response plans |
| Administrative | Policies and processes | Security policies, reviews, and procedures |
| Technical | Hardware-based controls | Physical firewall hardware, servers |
| Logical | Software-based controls | Firewall software, access control systems |
| Physical | Physical security measures | Fences, security guards, locks |
Security controls should be monitored and measured for their effectiveness.

Two pillars that control have:
The functional aspect of a control is whatever its meant to do. Control performs the function it was designed to address/does what it is meant to do. For example, a firewall filtering traffic between different subnets.
The assurance piece of the control is what tells us if its working or not. Control can be proven to be functioning properly on an ongoing basis. Usually proven through testing, assessments, logging, and monitoring, etc.
overview of risk management:
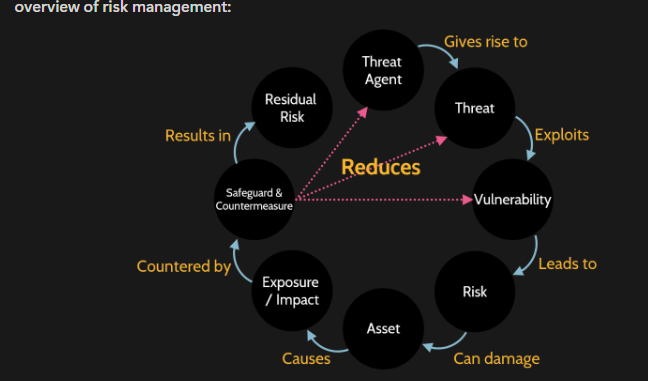
Threat Agent (attacker, hurricane, fire)
↓
Threats (potential dangers)
↓
Vulnerabilities (weaknesses)
↓
Risk
↓
Asset
↓
Impact/Exposure (loss of reputation/integrity/confidentiality)
↓
Safeguards & Countermeasures (prevention)
- A threat agent is someone or something that will cause a threat (e.g., an attacker, hurricane, or fire)
- Threat agents create threats, which are any potential dangers
- Threats can exploit vulnerabilities, which are existing weaknesses
- These vulnerabilities lead to risks
- Risks have the potential to damage assets
- Assets are anything of value, and damage to them causes:
- Impact/exposure, which may include: • Loss of reputation • Loss of integrity • Loss of confidentiality
- These are countered by safeguards and countermeasures that aim to prevent risks
Selecting Controls:
How much security is enough? Balance between the cost to protect an asset against the level of acceptable risk.
What do you need to know from the metrics to make good business decisions? This would mean picking the right metrics & reporting them to the right people.
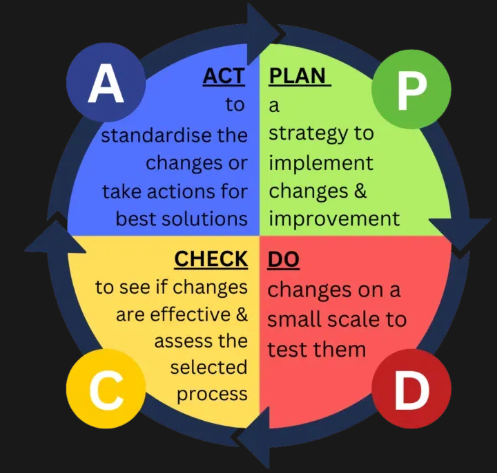
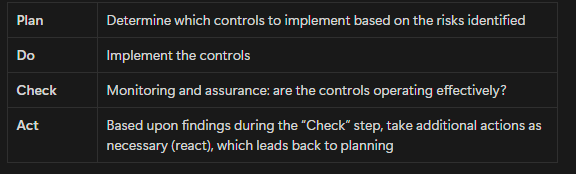
Another important aspect is continuous improvement. Its a continuous process; the environment is constantly changing, there are new threats and new vulnerabilities, and the threat landscape is constantly changing. A new asset, a new vulnerability, should trigger the risk management process.
Risk management Supply Chain
Organizations must thoroughly assess their supply chain by identifying all third-party service providers and conducting comprehensive risk assessments for each. This includes evaluating risks associated with outsourced processes and data, implementing appropriate risk treatment strategies, and establishing controls.
However, managing these risks can be challenging since organizations have limited control over their service providers' security measures and data handling practices. So its a big challenge to identify the contracts and make sure the SLAs, PLAS, whatever contracting vehicle the organization is using make sure its explicitly stated what controls are in place to mitigate the risks that the organization is concerned with.
Risk frameworks: Allow the organizations to have a set of guidelines to put in place a risk management process. Frameworks provide comprehensive guidance for structuring and conducting risk management.
Ex: COBIT, COSO, NIST 800-37, ISO 31000.
NIST 800-37 (RMF)
In the 7 Steps of the RMF, it is important to know the order.
- Prepare to execute the RMF—the organization evaluates the risk associated with a particular system.
- Categorize the information systems. Determine the adverse impact to operations, assets, individuals, etc. With respect to the loss of CIA of organizational systems.
- Select security controls; select the appropriate mitigation controls to mitigate the risks in step 2.
- Implement Security Controls: Implement controls and document in a baseline configuration the specific details of the control implementation.
- Assess Security Controls: Check if these controls are implemented correctly, and are they mitigating the risks that we identified in step 2?
- Authorize Information Systems: Provide accountability by requiring senior management; the person who is accountable for the system makes this call. The owner.
- Monitor Security Controls: Maintain ongoing situational awareness about the security and privacy posture of the information system and the organization in support of risk management decisions.
