In this lab walkthrough, your team is setting up a new Kubernetes cluster with two controllers and two worker nodes. The team has already created a set of client certificates to allow different components of the cluster to authenticate, but they need a set of kubeconfig files to be created using these certificates. Your task is to generate the kubeconfig files that will be used to set up the Kubernetes cluster.
The following kubeconfig files need to be created:
- Kubelet (one kubeconfig for each worker node)
- Kube-proxy
- Kube-controller-manager
- Kube-scheduler
- Admin
- Client certificates have already been created. They can be found in
/home/cloud_useron the workspace server
Controllers:
Hostname: controller0.mylabserver.com, IP: 172.34.0.0
Hostname: controller1.mylabserver.com, IP: 172.34.0.1
Workers:
Hostname: worker0.mylabserver.com, IP: 172.34.1.0
Hostname: worker1.mylabserver.com, IP: 172.34.1.1
Kubernetes API Load Balancer:
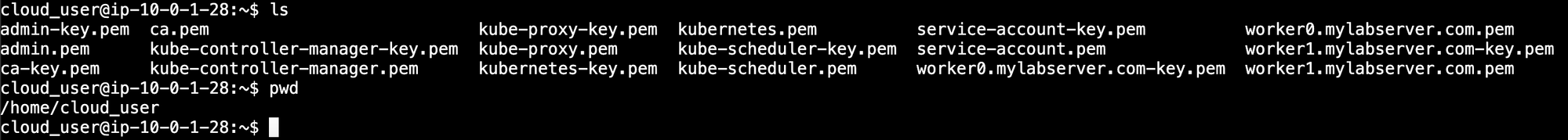
Hostname: kubernetes.mylabserver.com, IP: 172.34.2.0- We connect to the cloud machine and perform a ls and pwd command to verify the files we will be working with.
- We will generate a variable with the Kubernetes API Load Balancer: 172.34.2.0, Kubernetes will access this Kubernetes API.
- We will now generate configurations for worker1.mylabserver.com and worker0.laberserver.com
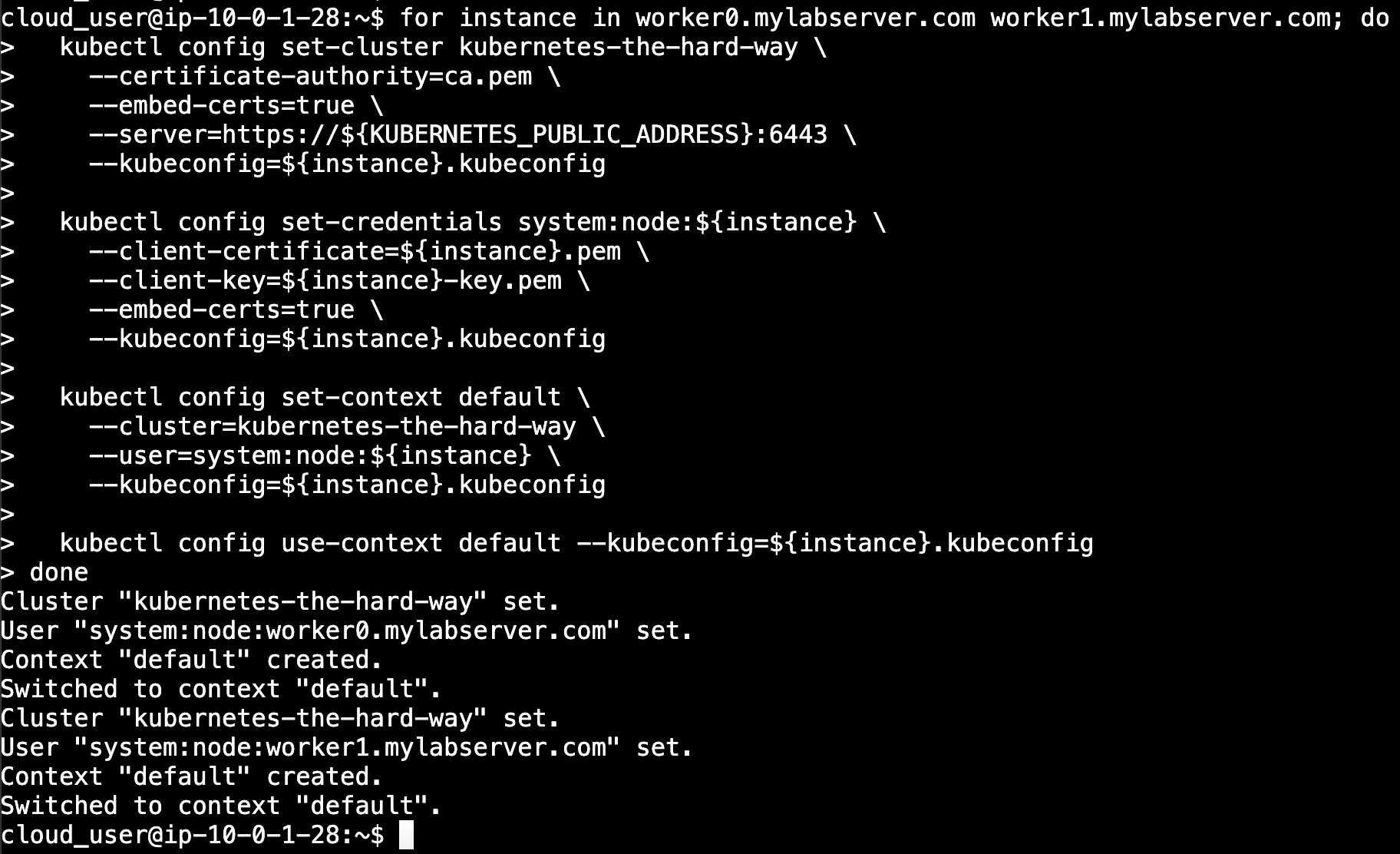
In this code we reference the load balancer IP address by the variable KUBERNETES_PUBLIC_ADDRESS, the certificate file is also referenced with the corresponding instance, ex: worker0.mylabserver.com & worker1.mylabserver.com, and towards the end the .kubeconfig is created according to the instance name.
Next we will generate a kube proxy config, which will call on the Kubernetes API, so the load balancer IP is referenced in the following configuration command:
KUBERNETES_PUBLIC_ADDRESS=172.34.2.0
{
kubectl config set-cluster kubernetes-the-hard-way \
--certificate-authority=ca.pem \
--embed-certs=true \
--server=https://${KUBERNETES_PUBLIC_ADDRESS}:6443 \
--kubeconfig=kube-proxy.kubeconfig
kubectl config set-credentials system:kube-proxy \
--client-certificate=kube-proxy.pem \
--client-key=kube-proxy-key.pem \
--embed-certs=true \
--kubeconfig=kube-proxy.kubeconfig
kubectl config set-context default \
--cluster=kubernetes-the-hard-way \
--user=system:kube-proxy \
--kubeconfig=kube-proxy.kubeconfig
kubectl config use-context default --kubeconfig=kube-proxy.kubeconfig
}
In the following configuration we will reference the Kube-controller API directly as localhost (127.0.0.1), this will generate a Kube-controller-manager .kubeconfig:
{
kubectl config set-cluster kubernetes-the-hard-way \
--certificate-authority=ca.pem \
--embed-certs=true \
--server=https://127.0.0.1:6443 \
--kubeconfig=kube-controller-manager.kubeconfig
kubectl config set-credentials system:kube-controller-manager \
--client-certificate=kube-controller-manager.pem \
--client-key=kube-controller-manager-key.pem \
--embed-certs=true \
--kubeconfig=kube-controller-manager.kubeconfig
kubectl config set-context default \
--cluster=kubernetes-the-hard-way \
--user=system:kube-controller-manager \
--kubeconfig=kube-controller-manager.kubeconfig
kubectl config use-context default --kubeconfig=kube-controller-manager.kubeconfig
}
The same process will be repeated as kube-scheduler, same as kube-controller manager just with a different name:
{
kubectl config set-cluster kubernetes-the-hard-way \
--certificate-authority=ca.pem \
--embed-certs=true \
--server=https://127.0.0.1:6443 \
--kubeconfig=kube-scheduler.kubeconfig
kubectl config set-credentials system:kube-scheduler \
--client-certificate=kube-scheduler.pem \
--client-key=kube-scheduler-key.pem \
--embed-certs=true \
--kubeconfig=kube-scheduler.kubeconfig
kubectl config set-context default \
--cluster=kubernetes-the-hard-way \
--user=system:kube-scheduler \
--kubeconfig=kube-scheduler.kubeconfig
kubectl config use-context default --kubeconfig=kube-scheduler.kubeconfig
}
Now we will do the same process for kube-admin:
{
kubectl config set-cluster kubernetes-the-hard-way \
--certificate-authority=ca.pem \
--embed-certs=true \
--server=https://127.0.0.1:6443 \
--kubeconfig=admin.kubeconfig
kubectl config set-credentials admin \
--client-certificate=admin.pem \
--client-key=admin-key.pem \
--embed-certs=true \
--kubeconfig=admin.kubeconfig
kubectl config set-context default \
--cluster=kubernetes-the-hard-way \
--user=admin \
--kubeconfig=admin.kubeconfig
kubectl config use-context default --kubeconfig=admin.kubeconfig
}
With this, we have set up all the necessary kube config files in order to set up a Kubernetes cluster.
